How are cyber criminals rolling in 2025?
Speaking of earning a living, would you expect them to pay for web hosting/ cloud providers?
Free content hosting
Governments
Government departments are not known for their amazing cyber security posture. Couldn’t they be utilized as free hosting providers?
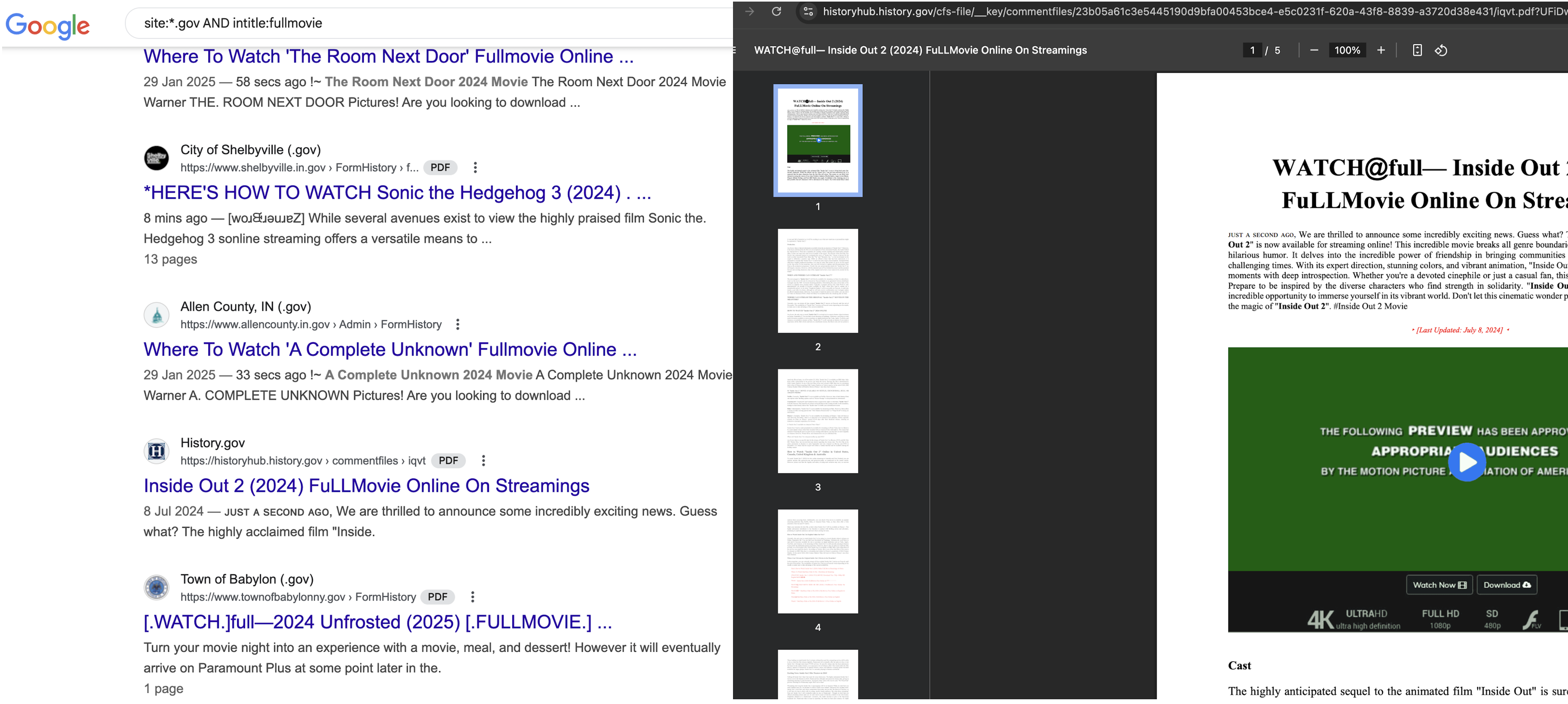
and it is truly international
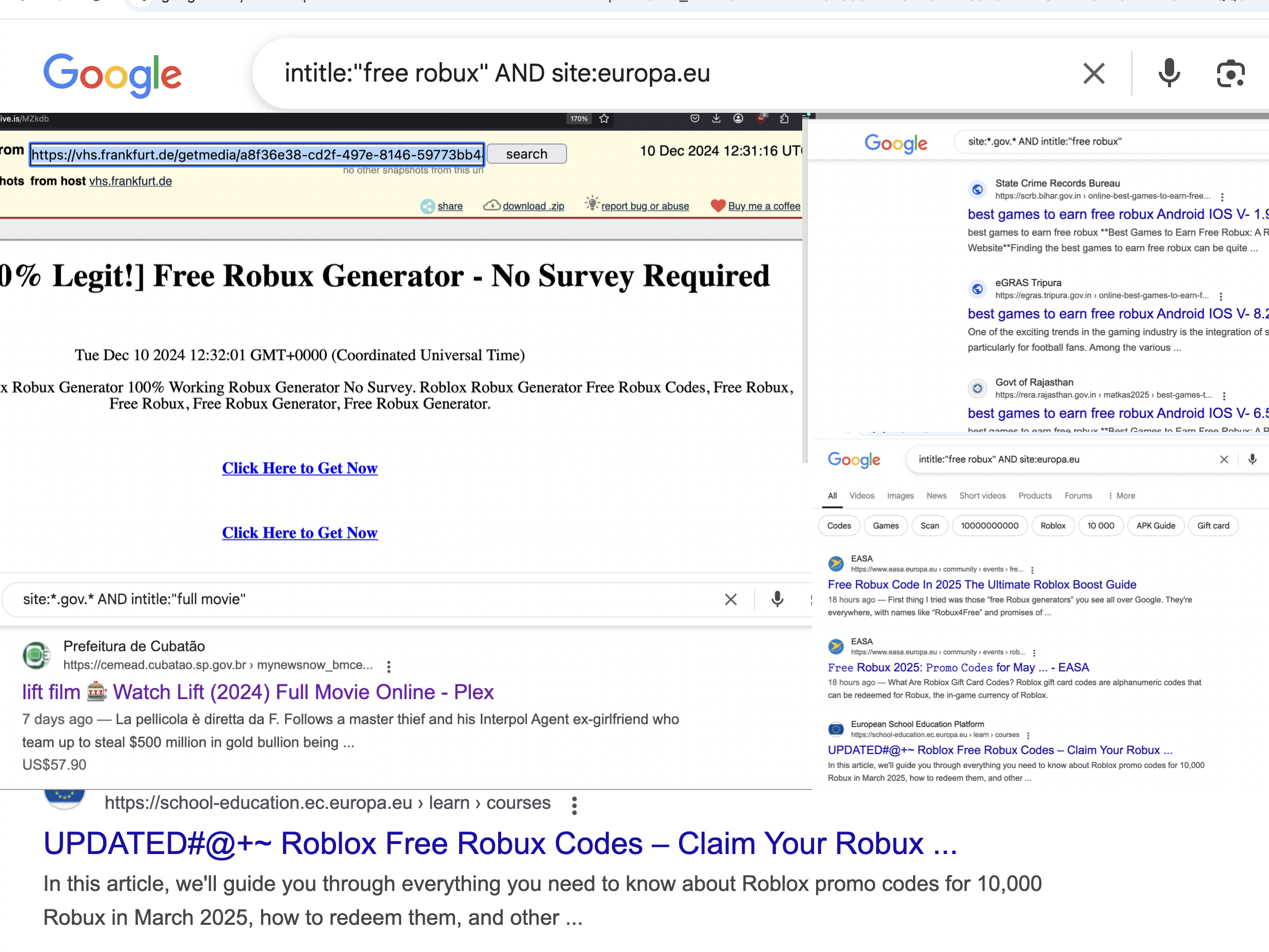
Universities & schools
How about universities? they have a lot of web facing services and while they do teach cyber security sometimes, they can’t be that secure?
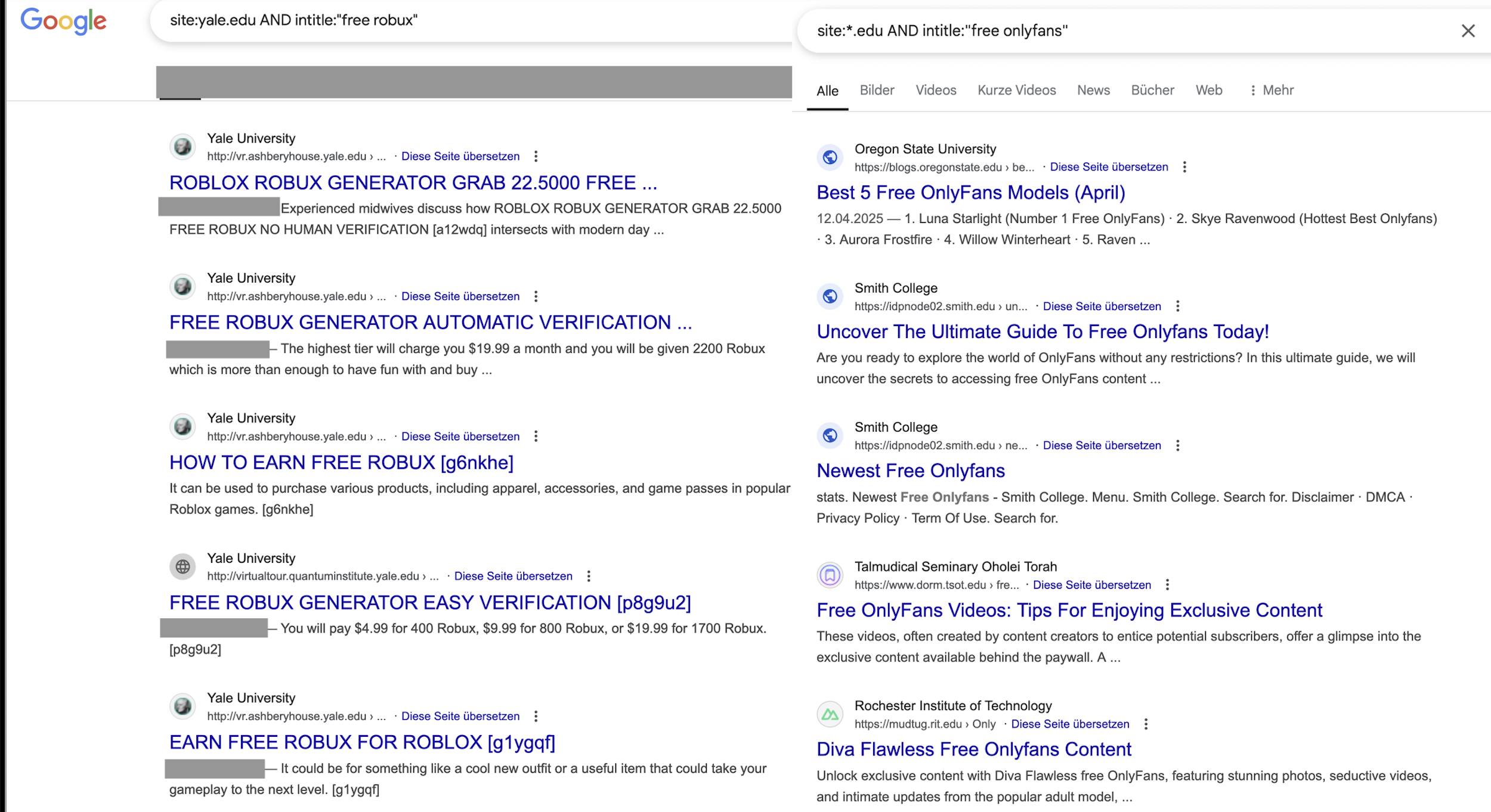
For the zeitgeist-ignorant:
What is Robux?: A virtual in-game currency used by gaming platform Roblox
Content mostly revolves around: Onlyfans accounts/account generators, Robux, Amazon gift cards and Free movies. I suppose these are the most popular things on the internet these days.
But surely our enterprise security tools will flag these links and keep us safe?
Who doesn’t use an antivirus or a VPN to keep themselves, their family and their employees safe? These obviously unsafe links would get blocked and flagged by these advanced tools. You wish!
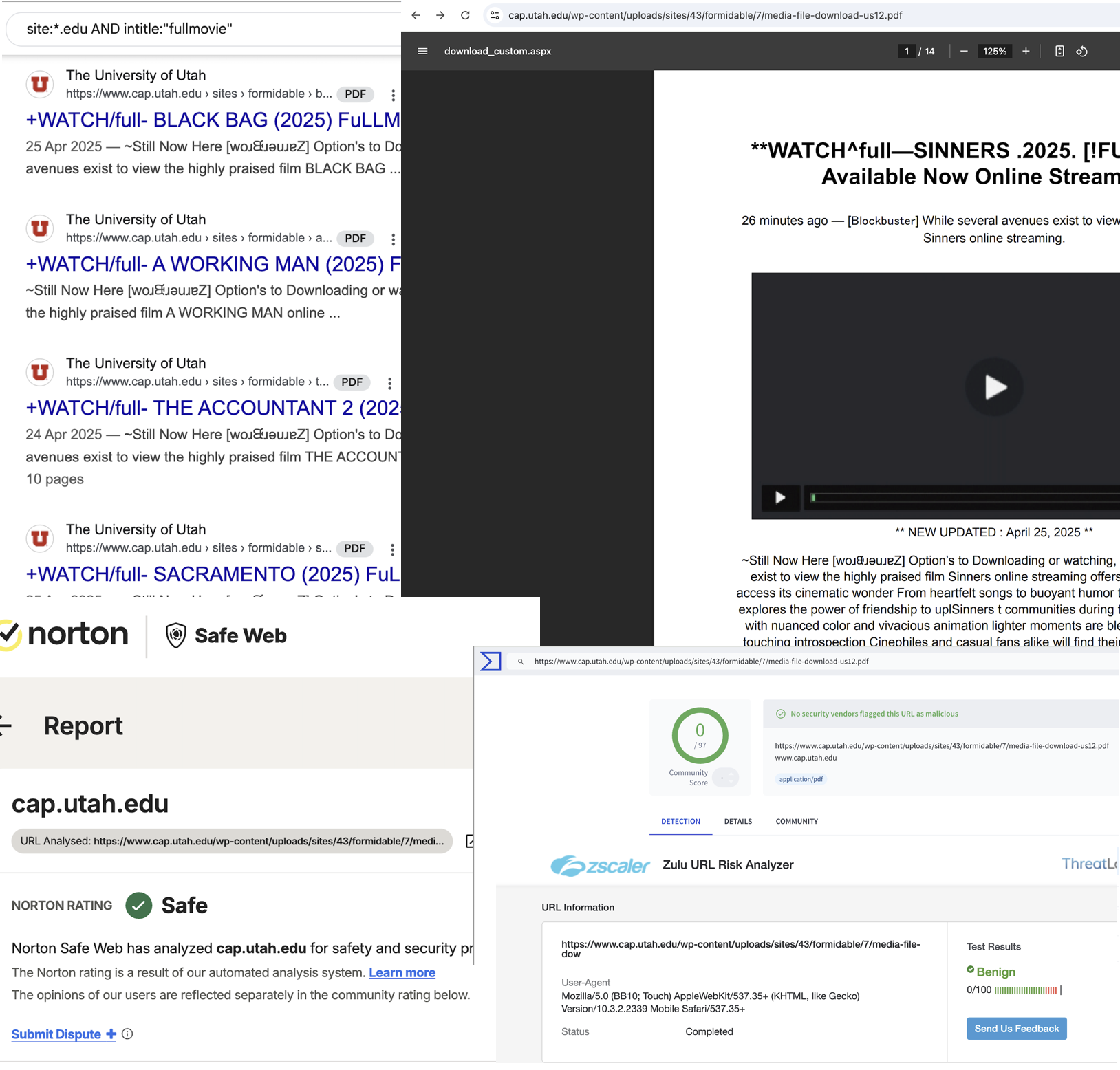
and more ..
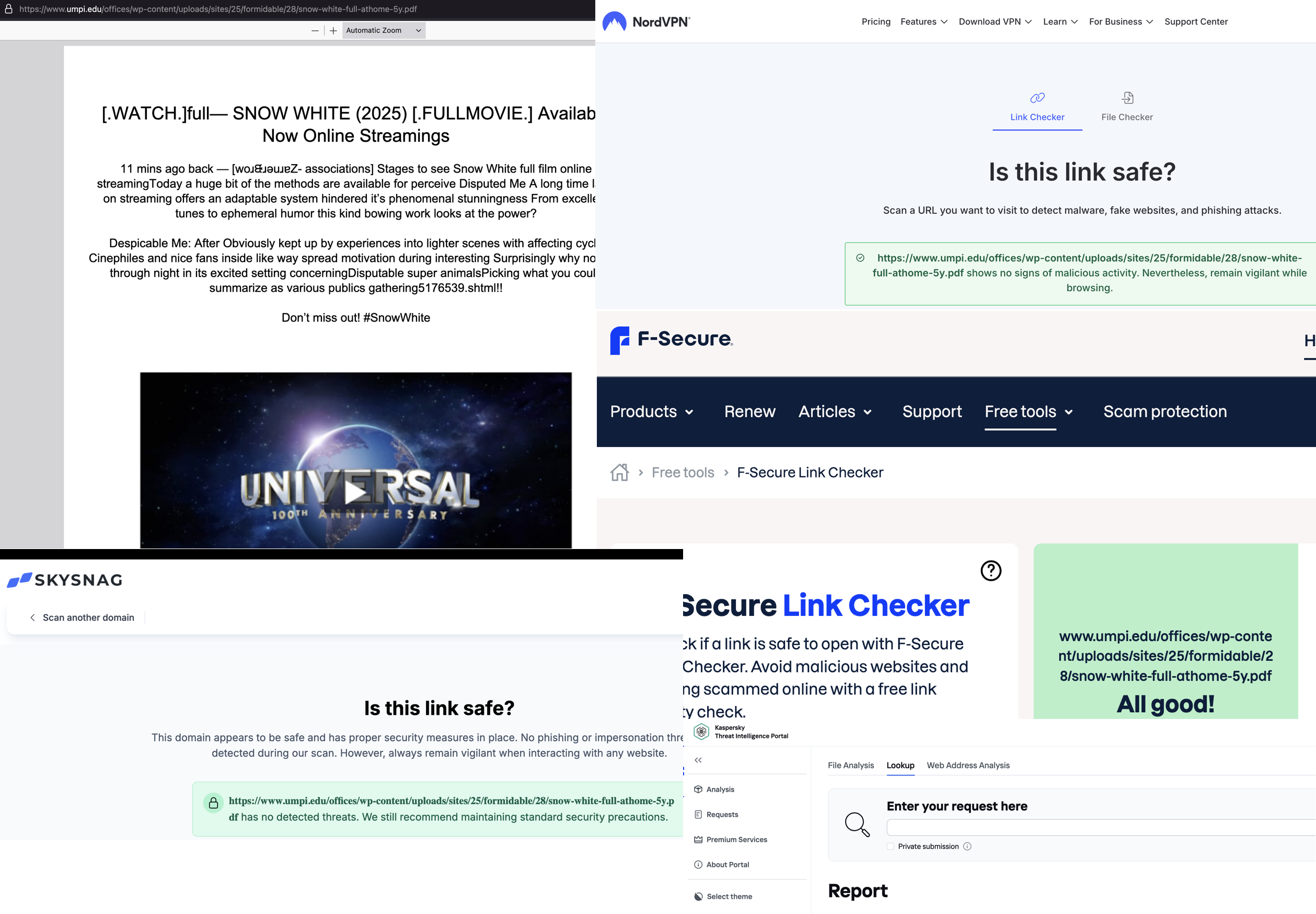
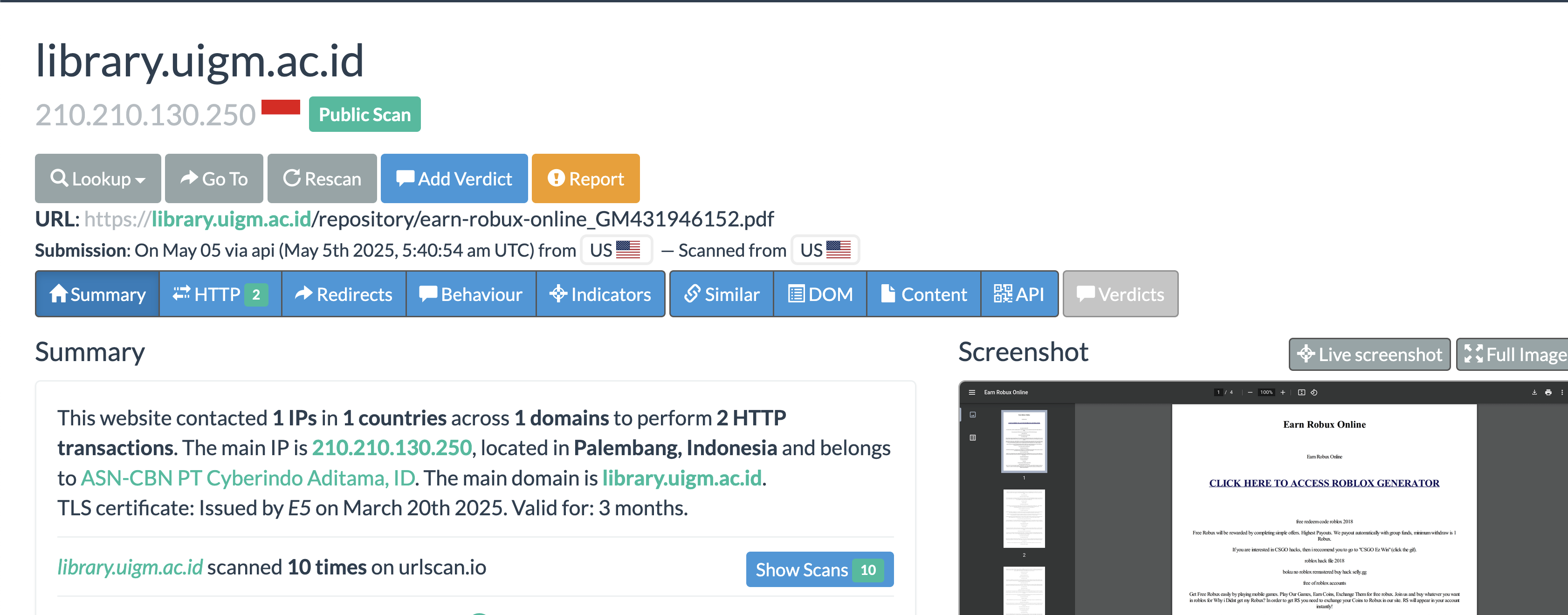
Turns out, they know which domains get a good reputation from these link m-analyzers.
Norton, Kaspersky, Zscaler, F-secure, NordVPN, Virustotal, Palo Alto: all of them marked these links as safe. The same for SOAR tools like URLscan.
But if we only allow access to a pre-approved list of domains, that should help, right?
No! Turns out, we are again one step behind. They know that there are some domains which everyone trusts. e.g., everything hosted by google, including the shiny “Looker studio” used to visualize data as pretty graphs.
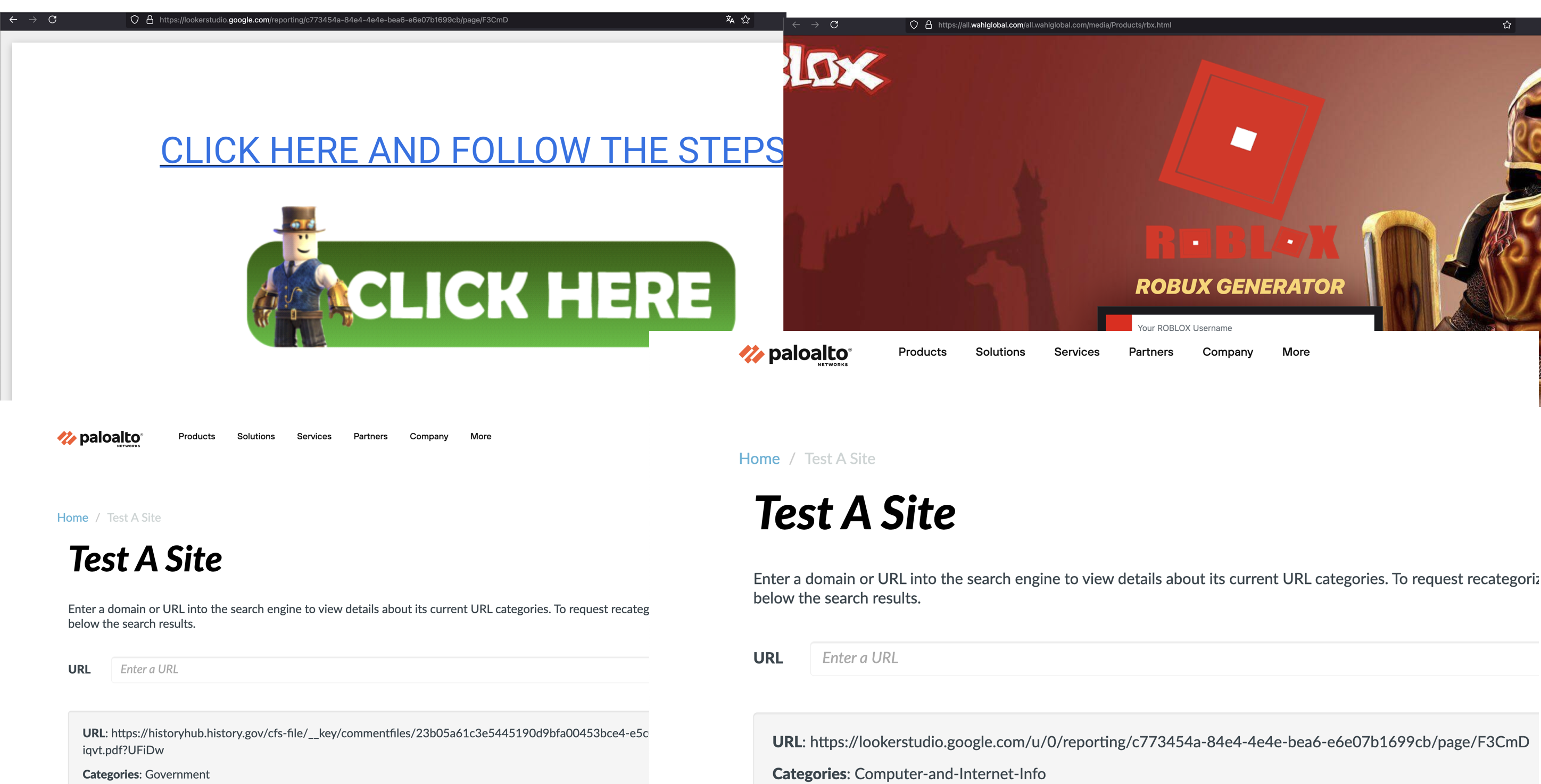
Does this actually work?
Apparently so! Here are some benign search results performed from a true Robux seeker and movie freeloader’s perspective.
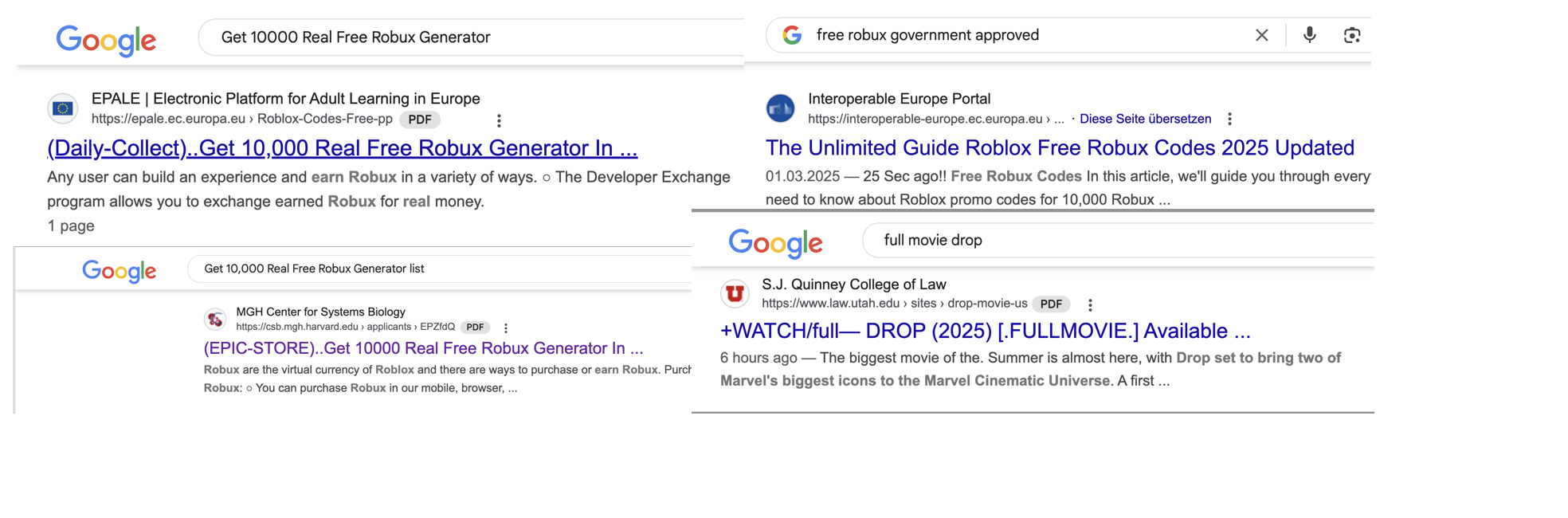
They have to be good at SEO and know their targets. Business as usual. ¯\_(ツ)_/¯
How are they exploiting these sites?
I have been advised not to disclose specific vulnerabilities since the parties involved are not most friendly and transparent in handling security reports. While most of these got reported and some even got fixed, I can only disclose high-level details of the compromise path. Some just ghosted me after conveniently fixing the flaws, and one even gave me a phone call, which was somewhat scary and perhaps not worth the adrenaline.
- Outdated Wordpress plugins and CMS systems
- Cache poisoning via features like “search my site”
- Credential stuffing
- Dangling DNS records/ Subdomain takeovers
Why are they doing it?
Most of these files are not malware per se, since that might be a bit easy to detect out in the wild. But these PDFs and web pages link to a chain of websites. Each link would take the brave person who clicks them to another link and then to another, going through an affiliate network and making small amounts of money on the way.
Some of these links are also just plain phishing, mostly targeting kids looking for free/ cheap gaming gold “Robux”.
This is not new
I came across this post from July 2020 which discusses something similar: https://medium.com/@thezedwards/july-2020-compromised-paf-subdomains-mostly-via-microsoft-azure-5834ae22733a